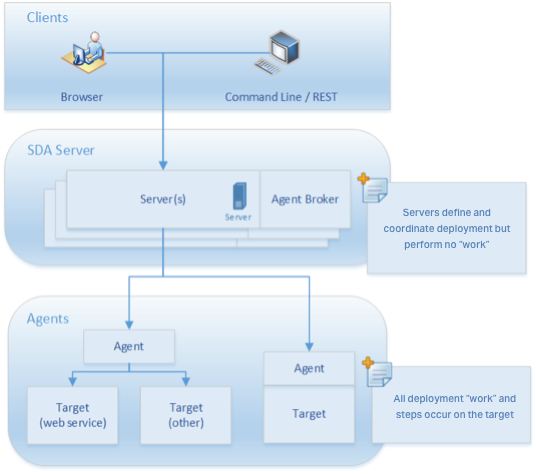
Deployment Automation can be used in a simple configuration for individual teams. It can also scale to support enterprise-grade requirements: horizontal scalability, enterprise-grade security, performance, and high availability.
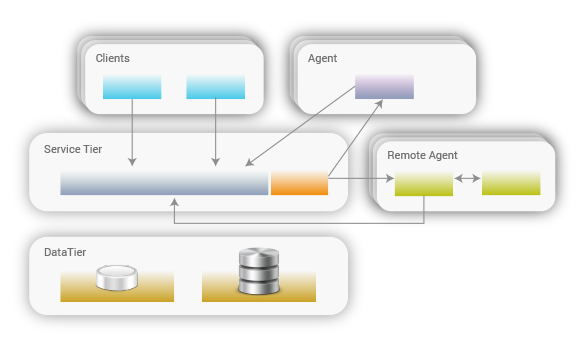
Deployment Automation has four primary components, and each can be logically and physically separated to support pre-existing, operationally-defined infrastructure requirements.