With Micro Focus Data Access Governance (Powered by File Reporter), organizations have the ability to identify access permissions to the largest and oftentimes most vulnerable data segment—unstructured data. Through integration with Micro Focus Identity Governance, these same organizations can also expand the capabilities of access reviews so that folders containing potentially confidential, sensitive, or regulated files can be easily reviewed to see user access permissions and if those permissions need to be kept, removed, or changed.
Through Data Access Governance, you specify the target paths for review. The paths then appear in the Identity Governance interface and can be reviewed the same way you perform an application review.

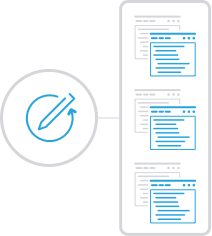
Through the Permissions by Path report, determine who can access a specific folder, the effective NTFS permissions enabling that access, and how those permissions are derived.
Through the Permissions by Identity report, identify all of the network folders a specific user has access to and the explicit NTFS permissions of that user.

Historic Comparison reports specify the differences in permissions of the same target path between two points in time.